Difference between revisions of "SAML"
Wikidevuser (talk | contribs) |
Wikidevuser (talk | contribs) |
||
| Line 101: | Line 101: | ||
:{| border="1" cellpadding="5" cellspacing="1"| | :{| border="1" cellpadding="5" cellspacing="1"| | ||
|- align="center" | |- align="center" | ||
! SLO !! | Session limit !! | | ! SLO setting!! | Session limit setting !! | Behavior | ||
|- | |- | ||
| OFF || OFF || | | SLO OFF || Session limit OFF || Only AgileApps session logout. Users can log in with any number of sessions. | ||
|- | |- | ||
| OFF || ON || Number of | | SLO OFF || Session limit ON || Number of active AgileApps sessions limited based on session limit count value. AgileApps session logout for the oldest session when the limit is reached. | ||
|- | |||
| SLO ON (Front Channel) || Session Limit OFF || No session limit. Only AgileApps session logout. | |||
|- | |||
| SLO ON (Back Channel) || Session Limit OFF || No session limit. IDP logout and AgileApps session logout. | |||
|- | |||
| SLO ON (Front Channel) || Session Limit ON || Number of active AgileApps sessions limited based on session limit count value. AgileApps session logout for the oldest session when the limit is reached. Choosing "Logout All" will perform only AgileApps sessions logout. | |||
|- | |||
| SLO ON (Back Channel) || Session Limit ON || Number of active AgileApps sessions limited based on session limit count value. IDP logout and AgileApps session logout for the oldest session when the limit is reached. Choosing "Logout All" will logout all IDP sessions and AgileApps sessions. | |||
|} | |} | ||
Revision as of 12:15, 11 January 2024
Security Assertion Markup Language (SAML) is an XML based standard for exchanging authentication and authorization data between security domains. The Service Provider must enroll with an Identity Provider (IdP) and obtain an Issuer URL.
Working with SAML
An enterprise application contains a link to the AgileApps Cloud platform. When a user who has logged on to the enterprise platform clicks the link, he can automatically log in to the AgileApps Cloud platform without any additional authentication. For example, if an employee who has logged on the ABC Company corporate website clicks the link to the AgileApps Cloud platform on the landing page, he can log on to the AgileApps Cloud platform automatically without a second log in.
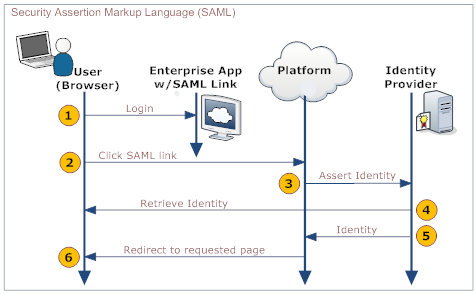
The following diagram explains the process:
User Your organization's web application Platform IdP 1. Log in to a web application provided by your organization - Provides a link to the platform's SAML handler (generated by the platform when SAML is configured)
- Includes the desired platform target page as an argument in the link
2. Click the link that directs to the SAML handler 3. Send an assertion to the IdP 4. Retrieve and validate the user's identity 5. Send the user's identity to the platform 6. Redirect the user to the appropriate page
Enabling SAML
- Click
 > Administration > Account Management > Single Sign-On Settings.
> Administration > Account Management > Single Sign-On Settings. - Click the [Edit] button.
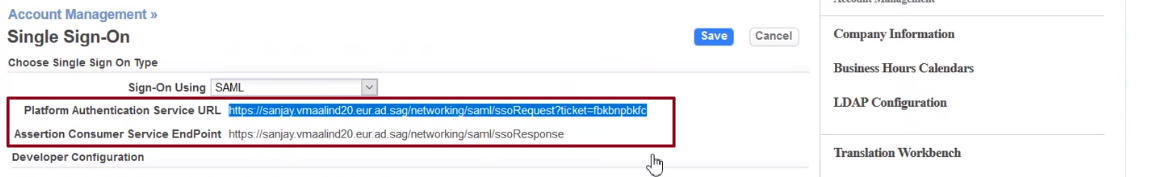
- Choose SAML from the Single Sign-On Using drop-down list. Selecting SAML automatically displays the Platform Authentication Service URL and the Assertion Consumer Service EndPoint fields below the drop-down list.
- Fill in the SAML Settings.
- Click [Save].
SAML Settings
- Platform Authentication Service URL
- To start the SAML authentication flow, copy this URL into your browser's address bar.
- Assertion Consumer Service Endpoint
- This URL needs to be configured in your Identity provider.
- SAML Version
- The default SAML version is 2.0
- Issuer
- This field contains the IdP's URL. After configuring the IdP for the tenant, copy the URL and paste it in this field. This URL is the SAML-response-issuer-URL.
- SAML Third Party authentication URL
- This field contains a URL (IdP single sign-on URL) which is used to authenticate a user or maintain a user's credentials. You might want to configure the IdP before you fill this field.
- Syntax:The URL and Port Number must be specified using a FQDN or an IP address, for example:
- www.abc.com:9090
- 192.168.1.10
- abc.def.com
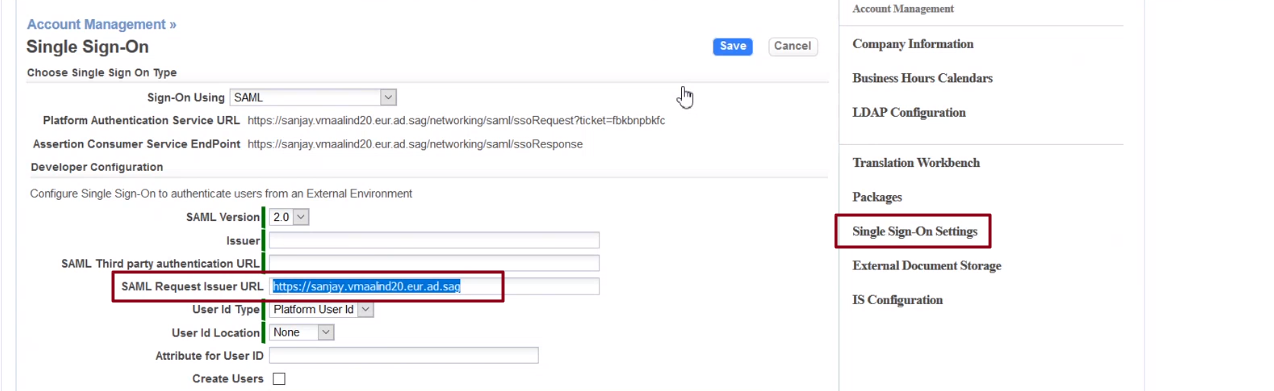
- SAML Request Issuer URL
- This field contains a unique value which identifies the service provider, for example: http://yourCompany.agileappscloud.com.
- User Id Type
- Determines the type of identifier.
- Choose either Platform User Id or Federated Id.
- Platform User Id is the username of the user that is logged in, while Federated Id acts as the user's authentication across multiple IT systems or organizations.
- For more information on Federated ID, see Federated Identity.
- User Id Location
- Specifies an attribute tag that defines the location of the User Id.
- Choose either Subject or Attribute.
- Attribute for User ID
- Specify the IdP attribute that contains a platform User ID.
- If the User ID attribute is empty or does not match an existing user, either login fails or AgileApps creates a new user based on the Create Users flag.
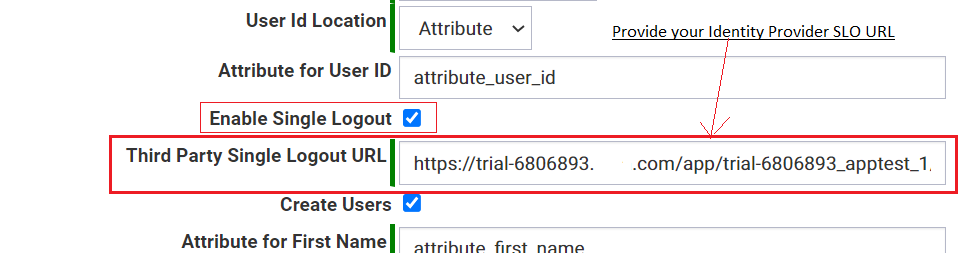
- Enable Single Logout
- Enable this if you want to provide Single Logout for the users.
- Third Party Single Logout URL
- You must provide the Single Logout URL provided by the Identity Provider.
Logout Method:
Configure the logout method based on the support provided by the IDP. There are two logout methods available:
- Front-Channel Logout: When a user clicks on the logout option available on the Dashboard or Configuration pages, this method utilizes browser support to forward single logout requests and receive logout responses from the IDP. The Http-Post binding method is adopted for the front-channel method.
- Back-Channel Logout: This method is adopted for session management capability. When a user chooses to perform a logout from the SSO session in the session list, the AgileApps server sends a logout request to the IDP through the SOAP binding method. If session limit is reached for SSO sessions, the default and only applicable option is to "Auto logout the oldest session".
Check out the below possible scenarios for SSO, SLO, and Session management configurations.
SLO setting Session limit setting Behavior SLO OFF Session limit OFF Only AgileApps session logout. Users can log in with any number of sessions. SLO OFF Session limit ON Number of active AgileApps sessions limited based on session limit count value. AgileApps session logout for the oldest session when the limit is reached. SLO ON (Front Channel) Session Limit OFF No session limit. Only AgileApps session logout. SLO ON (Back Channel) Session Limit OFF No session limit. IDP logout and AgileApps session logout. SLO ON (Front Channel) Session Limit ON Number of active AgileApps sessions limited based on session limit count value. AgileApps session logout for the oldest session when the limit is reached. Choosing "Logout All" will perform only AgileApps sessions logout. SLO ON (Back Channel) Session Limit ON Number of active AgileApps sessions limited based on session limit count value. IDP logout and AgileApps session logout for the oldest session when the limit is reached. Choosing "Logout All" will logout all IDP sessions and AgileApps sessions.
- Create Users
- Check this box to create a new user if AgileApps does not recognize the User ID.
- Attribute for First Name - The name of the SAML attribute that designates the user's first name.
- Attribute for Last Name - The name of the SAML attribute that designates the user's last name.
- Attribute for Email - The name of the SAML attribute that designates the user's email address.
- Default User Type - This field is used to specify the type of the user to be created.
- Choose either Platform User or Site User. The platform users are regular users in the platform while the site users have the similar behavior as portal users in the platform.
- When Site User is selected as the Default User in this SAML-SSO screen
- a. Only the Default Team is used for user creation. Other settings like default access profile, default application, and default role will be ignored.
- b. The created users will have same default settings as Access Profile (Portal User Profile) and Primary Team (Portal Users and Customers). Meanwhile, the user will also be a member of selected team in Default Team field (or any valid team-name provided through SAML attribute in ‘Attribute for Team’ field).
- Attribute for User Type- This field is used to specify the user-type to be created through SAML attribute. It is SITE for Site User and PLATFORM for Platform User. You might want to send the value for this attribute in the SAML response from the IdP.
- Default Team - This field is used to specify the default Team for the created user. For site users, the team will be a non-primary team.
- Attribute for Team- The name of the SAML attribute that designates the user's default team. For site users, the team will be a non-primary team.
- The attribute should contain a team name.
- Default Access Profile - This field is used to specify the default Access Profile for the created user. It is applicable only for Platform users.
- Attribute for Access Profile - The name of the SAML attribute that designates the user's access profile. It is applicable only for Platform Users.
- The attribute must contain an access profile's record ID.
- To get a record ID:
- a. Go to GearIcon.png > Access Management > Access Profiles.
- b. Modify the view to display Record ID, and copy the one you need.
- Default Application - This field is used to specify the default Application for the created user. It is applicable only for Platform users.
- This setting can be changed in the platform after user login.
- The user can change it in their Personal Settings. The admin can do the same in the Users page.
- To grant access to additional applications:
- a. A user record is created for the user in the platform after login.
- b. Use the Application Access page to specify the applications the user can access.
- Attribute for Application - The name of the SAML attribute that designates the user's application. It is applicable only for Platform users.
- The attribute should contain the application's name.
- Default Role - This field is used to specify the default Role for the created user. It is applicable only for Platform users.
- A user record is created for the user in the platform after login.
- The user can change it in their Personal Settings. The admin can do the same in the Users page.
- You can select multiple roles in this field.
- Attribute for Role - The name of the SAML attribute that designates the user's role in the application. It is applicable only for Platform users.
- This field can contain multiple role names separated by _::_
- For example, Agent_::_Manager
_
- Issuer Certificate
- Issuer certificate is used to sign and verify SAML messages. The certificate should be a valid x509 issuer certificate.
- Choose one of the following options:
- Navigate to the Issuer Certificate section, then select and load a file containing the Issuer Certificate (recommended)
- Paste the Issuer Certificate in the text area
User sync via SSO (SAML)
Overview
AgileApps now supports synchronizing user detail changes from identity providers. The following attributes are now synchronized:
- User basic information
- First name
- Last Name
- Email address
- Single or multiple Team updates in identity provider.
- Single or multiple role updates in identity provider.
Role and Team Sync
- For the user sync to function properly, the role and team should be delimited with the following character set _::_
Note:
- User sync is applicable only when Create User checkbox is enabled.
- Multiple team synchronization is supported through team attributes. However, a single team can be selected as default team in UI.
- User Sync will only be applicable for the users created through SSO flow, and not for the users created with REST API or UI flow.
- The primary team for the SSO Site users should always be Portal Users and Customers and the remaining teams will be assigned as secondary teams.
- Roles will not be synchronized for the SSO Site users.
- For SSO Platform users the first team provided in the SAML response will become the primary team, and the remaining teams will be assigned as secondary teams.
- During the user creation, the default User Type, Role, Team, Application and Access Profile are considered if
- The corresponding Attributes for the fields are empty or
- The value of the attribute is empty from the identity provider or
- The system does not find the corresponding value into the System database.
- The user sync for Teams and Roles will follow an override approach. The existing teams or roles for this user will be removed and the new teams / roles will be added which are provided as value in the corresponding attributes from Identity Provider.
- User sync will not succeed if the provided teams or roles in SAML attributes, do not exist in AgileApps.
- In these circumstances when user sync fails, open the browser's console and look for the response header SSOErrorMessage in order to analyze the fault.
Using SAML
To use single sign-on with SAML, create links that directs you to the platform's SAML handler and pass the desired destination page as an argument.
To create a link to the platform in your enterprise application:
- Copy the SAML link generated as the Platform Authentication Service URL while configuring SAML
- Add a done= argument to the link that specifies the target page in the platform
To create the done= argument:
- Go to the standard initial page using <syntaxhighlight lang="java" enclose="div"> servicedesk/index.jsp </syntaxhighlight>
- Go to the page that you want to target.
- Copy the URL from the browser's address bar.
- For old UI, edit the URL to remove <syntaxhighlight lang="java" enclose="div"> https://{yourDomain}/networking/ </syntaxhighlight>
Add the remaining as the value for done= parameter.
- For example: servicedesk/index.jsp#_a87199395ac14d01b3402a7915c0ff78/245418134 or pages/TestPage.jsp
- URL encode the link
- For more information, see URL Encoding.
So, the complete URL used to access AgileApps through SSO would look like:
- Old UI: <syntaxhighlight lang="java" enclose="div"> https://{serviceDomain}/networking/saml/ssoRequest?ticket=cnpkkccqsqscnp&done=servicedesk%2Findex.jsp%23_a87199395ac14d01b3402a7915c0ff78%2F245418134 </syntaxhighlight>
- New UI: <syntaxhighlight lang="java" enclose="div"> https://{serviceDomain}/networking/saml/ssoRequest?ticket=cnpkkccqsqscnp&done=https%3A%2F%2F{serviceDomain}%2Fagileapps%2Frecords%2Fdetail%2Fcases%2F558782450 </syntaxhighlight>
Important Notes
- AgileApps supports authentication for Platform Users and Site Users through any IdP like Azure AD, OKTA, OAM, PING, and so on
- If the user doesn't exist in AgileApps, a new user can be created by selecting Create Users check box and configuring the AgileApps-SSO-SAML screen
- AgileApps has an option for creating Platform Users and Site Users using the pre-stored attributes or parameters in the IdP
- Any unique name or ID provided as an attribute value in the 'Attribute for User ID' field in AgileApps-SSO screen is the username of the newly created user
- Any Attribute value sent from the IdP should contain Names instead of IDs, for example, Application Name, Team Name, Access Profile Name, and Role Name
- The default field value in SSO screen will be overridden with the corresponding attribute values if a valid attribute value is provided through the IdP
- First Name, Last Name, Email, and Username fields are read-only fields for the users created in AgileApps through SSO-SAML because the IdP will only be the source of identity for such users, hence these identification must not be modified from any other source except the IdP.
Note: The basic user information is synchronized during the login process through SSO. For more details, see User sync via SSO (SAML)
- The users created in AgileApps through SSO cannot reset their password